Build Your Own Independent Phone Network: Part 2

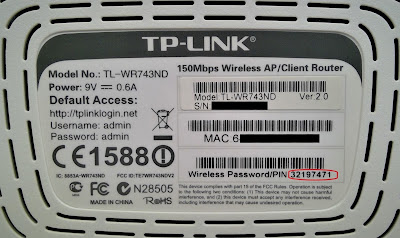
In the first part of this project , we completed all the prerequisites needed to build an offline independent phone network. We are now ready to finalize, launch, and use the network, which I will demonstrate in this post. Note that this post is best viewed on a PC as the code snippets are too large for smartphone displays.